Final Iteration Summary
The last iteration ended with us assigning our documentation tasks. I would like to thank to the group because they made todays presentation possible. Even though we had some ups and downs we had an acceptable ending to this iteration.
Hopefully we have convinced the client to buy our solution.
Updated and achieved requirements
Project owner: Red leader
Project customer: CompanyX.INC
Users: CompanyX employees.
Requirements:
-Functional
- The users should be able to access the internet.
- The users won’t have access to social networking websites like Facebook or Skype.
- Downloading files will have a size limit.
- Users don’t have the ability to install software on their working Pc’s
- The traffic will be monitored and analyzed.
- The company will offer acces to a web page.
- The Lan clients will be able to access the Samba file server.
- Webserver must be running and exposed to the external network.
- A firewall must be set up to limit traffic between the two networks.
- The firewall must be monitored.
- Proxy implemented to bypass the firewall.
-Non-Functional
- Offer a simple solution for connection to the Samba file server.
- The project should be cost effective.
- Hardware should be powerfull enough to handle the software.
- Secured connection to the Samba file server is available using VPN.
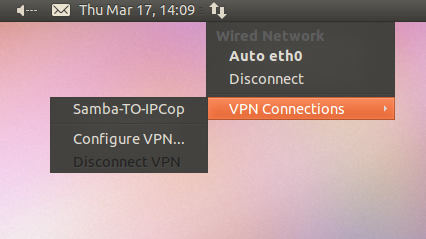
OpenVPN clients
Regarding OpenVPN clients these are the selected options:
Windows clients
For Windows clients there is the OpenVPN GUI for Windows:
The instalation is pretty straight forward, still just in case some pointers may be found here(also the way to make it work is also here):
http://thinkhole.org/wp/2006/03/28/ipcop-openvpn-howto/
!Through the Virtual Machine NAT connection there need to be a port forwarding rule set up for the port the VPN is using. Also there is required to modify the IP that the VPN client is connecting to:
-in the *.ovpn file you need to modify the “remote” line to point your IP from the local lan:
Linux clients
Linux has in its Repository a very nifty addon for the Network Manager called network-manager-openvpn:
Just to be on the safe side update your Repository so you know you will be getting the newest version:
sudo apt-get update
Installation:
sudo apt-get install network-manager-openvpn
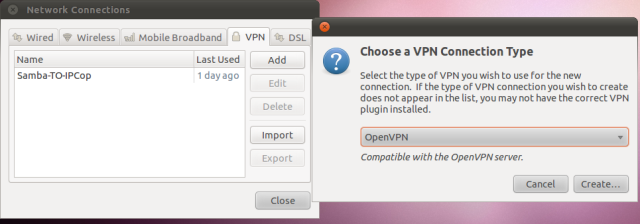
Using the network connections icon-> Go to VPN Connections -> Configure VPN…
Now Click the Add button and select OpenVPN connection:
Now here is the catch:
The Zerina OpenVPN add-on makes the certificates as 1 pk12 file.In order to work we need to break this down into 3 pieces. This is done with the following commands:
#Extracting CA certificate:
openssl pkcs12 -in myvpn.p12 -cacerts -nokeys -out myvpnca.pem
_^ file that we are extracting ^ new file where to extract
#Extract the Personal Certificate:
openssl pkcs12 -in myvpn.p12 -clcerts -nokeys -out myvpncert.pem
#Extract the Private Key:
-With password: openssl pkcs12 -in mydccert.p12 -clcerts -nocerts -out myvpnkey.pem
-Without: openssl pkcs12 -in mydccert.p12 -clcerts -nocerts -nodes -out myvpnkey.pem
http://www.carbm1.com/?p=184#comment-3996
A breviary with what each command means:
http://linux.die.net/man/1/pkcs12
#Assign them to their specific brackets:
Check the port that you are connecting by clicking the advanced button. It must be the same with the one assigned to the VPN server.
You can also import your configuration from the *.ovpn file, but you must change the extension to *.conf. Unfortunately the Extracting of the *.p12 file is not optional.
Mobile Android Phone
It accepts the normal configuration and pk12 files. Just importing them should make it work(Installation and testing of this has been carried out by Paul).
http://www.androidzoom.com/android_applications/communication/openvpn-installer_epia_download.html
Client for Mac
http://code.google.com/p/tunnelblick/
For the project we have the requirement of only the Windows and Android clients, the other two can be implemented if the client requires in the future.
File sharing and storage space
One of the requirements of this project was to find a way to give employees the opportunity to upload important files to a safe location accessible only by entering a username and a password. They have an assigned home directory on which they can only navigate forward and backward within that directory. The first solution that came up for this requirement was a FTP server with different accounts for every employee but some problems in setting up permissions for users appeared also some down sides of FTP were that it was a bit hard to use and that it wasn’t secure.
Another solution was to install a samba server. This provides folder like access to the assigned directory it also locks the client to its home directory exactly as needed. Further configuration was done by editing the “samba.conf” file to give clients write permissions within the folder.
Samba proved much more reliable and easy to use becoming a much better implementation in our project
Blue subnet
In the fourth iteration one of the tasks was to implement an wireless network for guests entering the comanys building. The problem was solved by configuring the blue interface of IPcop. The IP adresses are assigned using DHCP and also for the connection to work, in the firewall, a blue access rule needed to be set up.
Activating IDS (Intrusion Detection System) on IpCop
IPCop includes the Snort intrusion detection system, which is quite a powerful system for detecting various attacks on internal servers. Using IPCop to protect a servers on DMZ network you will find Snort quite useful. The added benefit of an IDS is that we can see what is passing through our network and attempt to isolate any traffic that appears malicious. This is important as it’s a function many firewalls lack (except those with layer-seven support, which are termed application-layer firewalls). Since firewalls work at the lower layers of
network communication their filtering rules are generally limited to IP addresses,
ports, time of day, and only a few other criteria.
IPCop makes setting up Snort very simple. Just go to the “IDS” tab on the IPCop menu under Services, and tick the “Enabled” box. To get latest snort rulsets you have to register in snort.org and generate Oink code. Check box “Sourcefire VRT rules for registered users ” since option with subscription is for those who pay. Save, Refresh, Download, Aply and chose which interfaces to monitor. Should look like this:

After that remember to check your log regularly at logs menu:
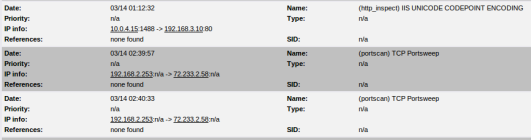
Next one need to set up log sending to remote server where it can be processed.
Reference:
Configuring IPCop Firewalls Closing Borders with Open Source ISBN 1-904811-36-1
![]() So far:
So far:
– Configure Blue Subnet
-Monitoring
-Connecting Phone VPN
-Vulnerability Test
-Log settings, log posibilities
-IDS
-Create Guest Subnet
-FTP connect to VPN (Alexandru)
-FTP security
So far these are the tasks defined for this iteration. Some in progress some(most!) hopefully done till monday.
Adding content filtering functionality to IpCop
To add content filtering functionality to IpCop you need to add Cop+ addon. Cop+ is a Dansguardian add-on for the IPCop firewall. You may choose other, but this one works pretty well. More info about Cop+ http://home.earthlink.net/~copplus/
Starting with instalation to IpCop box.
SSH in IpCop box and copy “copplusaddon-3.1.0.tgz” to root, download it at link above.
Extract package on your host pc, then ssh in ipcop, after that browse to “var/ipcop/” and copy copplus folder (which you get by extracting the downloaded archive) to ipcop box.
After that ssh in ipcop box and copy copplusaddon-3.1.0.tgz to root. Then extract and run setup.
# tar -xzvf copplusaddon-3.1.0.tgz
# cd var/ipcop/copplus/
# ./copplussetup
# logout
After that in ipcop panel should appear
After that you can proceed to configuring, its already predefined filters included, so if you want to ad some special phareses or domains, IP and so on, to be block, then you can do it by clicking on Blacklist edit and add some keywords that will be blocked. More about whats black, white and grey lists you can read when you click edit button.
In example we entered Facebook.com in black list so client cant access it. So when client will try to enter site, he will get message like this
You can check in logs about statistics of content blocking, in main page of content filtering choose DansGuardian Logs. For instance you want to see summary of denied requests, you click Denied and Run report.
This window will pop up and there you can see statistics of denied pages. You can see that google.com is on a block list, it is because client was requesting inappropriate search query that was blocked.
Then you click Trace and you can see who was who requested the page that was blocked.
![]()
OpenVPN addon install for IPcop
This will be more of a reference post in regards to “How to” install the Zerina OpenVPN add-on for IPcop. I will supplement with additional information to each link, as important points in the instalation directions or comments.
The first link is a step by step How to install Zerina on IPcop remotely and one of the software clients that we will be using for our Windows clients machines:
http://thinkhole.org/wp/2006/03/28/ipcop-openvpn-howto/
*Currently the software only supports Host-to-Net VPN configuration.
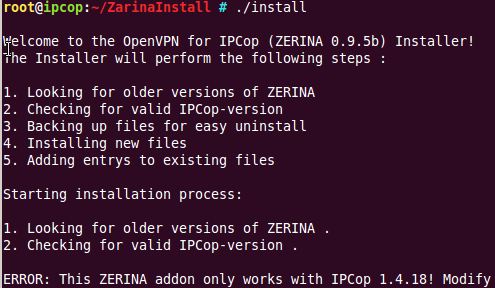
(4) There is a important issue in the instalation process at Step 4. If the version of IPcop is “incompatible” with the version of Zerina addon you will be prompted with the following:
If you have the newest version of IPcop it will without a doubt happen. Fortunately there is a very easy way to bypass this.
Using the text editor nano or any other text editor you are able to use modify the line from the code:
if [ ! “`echo $IPCOPVERSION | grep “1.4.15”`” ] ; then (instead of the 1.4.15 change it to the IPcop version you are using)

Alternatively comment (#) all of the following lines:
#if [ ! “`echo $IPCOPVERSION | grep “1.4.15”`” ] ; then
# echo
# echo “ERROR: This ZERINA addon only works with IPCop 1.4.15!\n”
# echo “Sorry. Please update your IPCop – visit www.ipcop.org!\n”
# echo “”
# exit 1
#fi
http://www.ipcops.com/phpbb3/viewtopic.php?f=8&t=11719
(5) Step 5 is very important: It has to generate a configuration file, which without you will not be able to have access to the export files for setting up your client machines(the actual process of installing and configuring will be covered in a different post).
Configuration guide to Zerina OpenVPN:
http://www.openvpn.eu/index.php?id=73&L=0
*It is possible to have small differences from what version you have installed in comparison to the actual tutorial pictures.The setup will be fairly the same.
Test the log file to see if everything and connect with the client installed on a machine from either the green or the orange network (isolates the problem if any involving the server configuration).
Snip of our configuration:
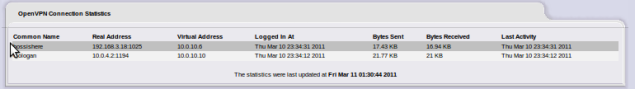
Clients connected
Statistics page with the client systems
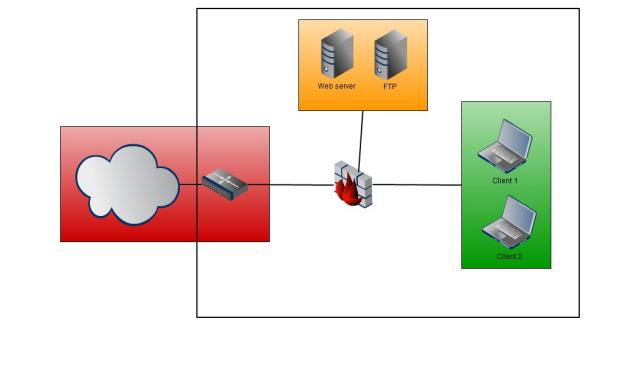
Port Forwarding(Part 2: IPcop)
In our DMZ setup there are 2 things that require to setup Port Forwarding for: the Webserver and the VPN(for the FTP server).
The process of port forwarding to the exterior of the virtual machine was covered in the first post regarding this.
For the actual network itself the VPN server installed has his own configuration settings, meaning IPcop will only require a single portforwarding rule for the Webserver.
The Firewall tab in the picture above has 4 submenus:
1) Port Forwarding – used to set port forwarding rules for the DMZ.
2)External Acess – this doesn’t have any effect to the DMZ zone (Green and Orange networks). It is used to gain exterior access to the actual firewall and it is only used for this purpose.
3)DMZ Pinholes – this is used if it is required to give access from the Orange to the Green network(considering our setup). It will not be used in our configuration.Using could have a high security risk involved with it.
4) Firewall Options – a menu that you can chose whether ping response is allowed or not.
More detailed information on the tabs and IPcop is found here:
http://www.ipcop.org/1.4.0/en/admin/html/section-firewall.html
Iteration 3
In PROGRESS:
Web proxy- Z
VPN- A
Logs possibilities- R
FTP security- P
IDS-B
IDEAS:
DMZ
FTP permissions
Log settings
Research solution (in general)
URL Filtering
Today we decided what will do what for this iteration. Then all tasks will be done our group will decide what other tasks should be implemented to the project.
Port forwarding (Part 1:connection through NAT)
This is a “How to” on port forward virtualbox. It comes as an addition to the short tutorial presented here: http://vojev.wordpress.com/2011/02/28/enable-port-forwarding-virtualbox/.
If you haven’t read it, it would be fairly wise to do so in the idea of understanding the things that i am going to express. *For getting access to VBoxManage commands you are required(in command line) to be in the folder where you have installed your VirtualBox.
Use Start -> Run and write: “cmd”.
 The above image describes the pathway to access my VirtualBox folder.The command cd is equivalent to change directory and the lines that precede it represent the path to get inside the folder that you are looking for.
The above image describes the pathway to access my VirtualBox folder.The command cd is equivalent to change directory and the lines that precede it represent the path to get inside the folder that you are looking for.
Now the configuration of the portforwarding rule in Vboxmanage is dependent to how you have setup of your network and the rules that you want to implement.For this i would like to reference the setup that we are having:
 Adapter 1:Pcnet-FAST III (Internal network, ‘Clients’) Adapter 2:Pcnet-FAST III(Internal network, ‘servernetwork’) Adapter 3:Pcnet-FAST III(NAT)
Adapter 1:Pcnet-FAST III (Internal network, ‘Clients’) Adapter 2:Pcnet-FAST III(Internal network, ‘servernetwork’) Adapter 3:Pcnet-FAST III(NAT)
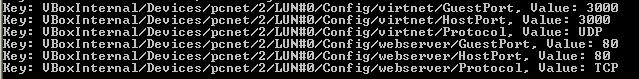
Now this is our DMZ firewall configuration, my third Adapter (Adapter 3) is NAT and it will be the one needed to modify because it will represent the link with the exterior. Breaking down some elements from the code that you will need to put for having portforward on the VM:
(1) This refers to the type of network card you are using: pcnet refers to either PCnet-FAST III or PCnet-PCI II(works for both). If you require for a diferent type it will have a diferent name, the two above are the most common to use. Check following link for another example of network card used and more information on the subject.
https://wiki.archlinux.org/index.php/VirtualBox#Accessing_server_on_VM_from_host
(2) This refers to the actual “slot” that you have assigned to the card.The enumeration of these start from zero.Basically: Adaptor 1 = 0, Adaptor 2=1 and continue to enumerate. The configuration with the 3 adaptors that i posted above mean that my NAT’ed adaptor is situated in the third slot. Meaning i will have to use the value “2″.
(3) This is the name(folder) of the actual rule that you are applying. It is usefull to know this if you require multiple ports to portforward, because you will have to define new names(folder) for them. !Putting a new rule over an existing one with the same command and trying new value at the end will simply modify the existing rule!
(4) When you are defining port forwarding you need to have add a command line for: GuestPort(value),HostPort(value) and Protocol(example UDP,TCP).
After defining these it is advised do the following two things:
1. check your entered code with:
![]() (Defined by ” “ : name of the VM)
(Defined by ” “ : name of the VM)
*it’s output (only showing relevant data) will be something in the lines of this:
2. The machine that you are making these modifications should neither be powered on or in a saved instantiation.
More info on VboxManage:
http://www.virtualbox.org/svn/vbox/trunk/doc/manual/en_US/user_VBoxManage.xml
Extend IpCop webproxy functionality
By default functionality of web-proxy in IpCop is not much customizable. For expanding this we need to install addon such as this: http://www.advproxy.net/download.html
In previous post I showed that you can install addons from there but somehow this addon panel does not like it and is saying that it is no authorized addon. So we can do it differently.
Installing the Advanced Proxy add-on for IpCop.
Using gFTP (linux) yourIpCop address (PORT 222), login to the IPCop and copy the ipcop-advproxy-3.0.5.tar.gz file to the IPCop root.
From the IPCop console or (using PuTTy (PORT 222)) log into IPCop and type:
# tar -xzvf advproxy-3.0.5.tar.gz
# cd ipcop-advproxy
# ./install
# logout
After this you should see Advanced proxy panel in your IpCop webpanel
Configuration is made easy, just set it up as you want and dont forget to force client to use proxy in browser.
We can also set file download limit size. You get this message in browser if you try to download file bigger than you defined in settings.
Adding addon panel to IpCop
I will show how to expand functionality of IpCop by installing addon panel, from where is possible to install addons to IpCop. This could be used for webproxy, VPN, logging and other functionality expantion.
Installing the “AddOns” Panel.
Enable Access for Copying files to IPCop and remote access.
Under the “System” tab in IpCop web panel, enable SSH Access by checking the first box. This will give you access to copy in the Add Ons file into the IPCOp server.
Downloading the AddOns panel.
The Add Ons panel must be downloaded to a PC, then copied using Winscp if you using windows or I could suggest gFTP for Linux to the root of the IPCop box.
From A PC which can connect to IpCop webpanel go to: http://firewalladdons.sourceforge.net and select the Add On Server version 2.3 from the download list. Follow the download from a mirror site and save the downloaded file to your PC. Using gFTP (linux) yourIpCop address (PORT 222), login to the IPCop and copy the addons-2.3-CLI-2b.tar.gz file to the IPCop root.
Installing the Add Ons panel.
From the IPCop console or (using PuTTy (PORT 222)) log into IPCop and type:
# tar -xzvf addons-2.3-CLI-b2.tar.gz
# cd addons
# ./setup -i
# logout
After this in your IpCop webpanel should appear menu like this:
In Addon panel just update list of addons and chouse one that’s for you.
My task
For this iteration my task was about windows and linux attributes. I have made on both operating systems two accounts: one is admin the other one is guest. Guest don’t have all permissions for downloading programs and installing it. Guest have permission for downloading photos, documents, pdf files (windows). On the linux machine i did the same. But it’s different than in windows for example if you are connect to the guest even if you have admin password and you are trying to install something into linux machine using terminal you won’t be able to install anything to your machine there will be written “try again later”.
But there is one problem: windows os can run programs from internet for example “putty” and files can be sent whatever user want. So for now i need research on how to deny running that sort of programs on pc.
Second iteration tasks A
Task’s assigned to me for second iteration we’re :
– VPN (research & implementation);
– port-forwarding ( how to in pfsense&normal NAT config ,how to for FTP & Webserver in the DMZ).[mostly to familiarize and catch up with the rest]
My progress for second iteration was basically none. My reasoning for this is bad planning of personal time and the fact that i misunderstood concepts like VPN in relation with our project.
1)In regards to Port-Forwarding: my understanding of the concept was ok , but when i had to actually implement it i have no luck in making it work.
*Update on this: Saturday after fresh install on Windows and putting to work the tips that Paul gave to me i got it working on pfsense & Ipcop (tested on webserver). Today it isn’t working anymore. Am still having bugs and being a novice on most things networks related, when i troubleshoot i screw them up even more.
2)Now VPN: In the second iteration my initial research was to use OpenVPN. Reasons we’re compatibility for both Linux and Windows clients, the fact that it works with SSL(Secure Sockets Layer), the amount of documentation available on the internet for it and in comparison with other options,for me made was the way to go.
(http://www.netheaven.com/TunnelTypes.html)
The issues that i had with this was that i had left a small timeframe to finish my task and my first understanding of the concept was the Host-To-Host setup of VPN wich i tried to implement like a ..(unrelated). The fact that i missunderstood the concept in regards to what we would have wanted to do for the project (roadwarrior setup) which made me totally waste iteration 2. This has neither been brought to the attention of the group or discussed in detail and for that and the fact that i haven’t achieved anything for the project in this iteration I would like to apologize, especially to Paul and Romanas.
I have not posted an entry for each task due to them being uncomplete and will make for them posts this iteration.
Comments from red leader
In my opinion the team didn’t understand the importance of working and solving tasks because it is not good to have only two members out of five showing something. I hope that for the next iteration everyone will set their priorities better and they won’t let the others down.
My task’s for second iteration
To have a fully functional network simulating the final product there was the need to install and setup several things. One of the task was to create a subnet containing the servers another one was to create a subnet for the clients and a more difficult one was to configure IPcop.
After creating the two subnets which was pretty straight forward the configuration of IPcop was the most difficult part especially configuration regarding the Orange subnet which holds for a DMZ area and which is the place where the servers are installed. The tricky part is that the orange network cant be accesed by the internet without special configuration and also it doesn’t get an IP address from the DHCP server on the IPcop the DNS server also has to be configured manually in order for it to have access outside. After solving all of these a port forwarding rule was added to give access to the webserver installed on it.
Iteration 2 Tasks
– FTP security – B
– VPN – A
– Research Solutions – Z
– Put together Subnets IPcop and Router in Virtual Box – P
– Web Proxy – Z
– Limit Attribute Windows – R
Iteration 2 Tasks in Progress
Web proxy;
Port Forwarding;net
Possibility of doing logs;
FTP security;
FTP Permission;
VPN;
Create subnet for servers;
Create subnet for clients;
Configure IPcop NICs;
Connect together PfSense, IPcop and subnets in Virtual Box;
Interview customer;
Research DMZ;
Limit user attributes in Linux;
Limit user attributes in Windows;
Iteration 1 conclusion
Overall progress of project is satisfactory. Tasks defined in beginning of iteration was completed in specified time line, sprint demo was made to show progress of project for customer. No particular problems were encountered during 1 iteration.
Iteration 1 progress
Research for firewall solution was made. Some sites with comparison of firewall found: 7 linux firewall comparison review. Conclusion in review taken in to account, Smoothwall and Monowall tested (installed firewall, server and client in virtualbox for testing). Smoothwall offers wide range of features, downside is for getting more nice features you have to pay. Monowall offers same functionality as Pfsense. Smoothwall includes a lot of features, such as build in proxy, IDS (snort) and etc and looks more like “Firewall”, so Monowall can be used as router software with same rule sets.
Also research made on IDS (intrusion detection systems). Take a look to 5 top IDS.
First iteration
So far, i have been reading about DMZ (demilitarized zone) how it works and how this network should be putted. Made some researches network, firewall, dirffrent kind of softwares fo security. I have in pc different web server running on Windows and Ubuntu like: Xampp and Apache .
First iteration progress
1) Installing Pf Sense and getting to know how to work with it.
– Installed and worked some basic configurations to connect to the internet. Researched on NAT, port forwarding.
-Installed Ubuntu for the configuration and connected to internet.
– Have done a bit of progress on web server and using port forward to connect to the web server.
2) Research on DMZ and firewalls in general.
– articles and wiki posts read.
– other materials sent by red leader read.
We shall see how much i know.
Requirements
Project owner: Red leader
Project customer: CompanyX.INC
Users: CompanyX employees.
Requirements:
Functional:
- The users should be able to access the internet.
- The users won’t have access to social networking websites like Facebook or Skype
- Downloading files will have a size limit.
- Users don’t have the ability to install software on their working Pc’s
- The traffic will be monitored and analyzed.
- Secured connection to the FTP is available using VPN.
- The company will offer acces to a web page.
- The Lan clients will be able to access the FTP server
Non-Functional
- Offer a simple solution for connection to the FTP server.
- The project should be cost effective.
- Hardware should be powerfull enough to handle the software.
First tasks in iteration proces
1.) Install Pfsense and FTP server
1.1.) Managed to try first to install Pfsense (freeBSD) in my Virtual Box.
Aim to Ping from inside to out. This seems to work.
1.2.) Then I installed a client (Ubuntu 10.10) in Virtual Box with FileZilla as a FTP Server. This gave me some troubles, which I have been trying reading about it, and as well solve.
2.) Research on DMZ (demilitarized zone) and firewalls in general
2.1.) The research on DMZ of the common ground from the issue how this work.
My fairly way how to understand the multiple layers of protection for the
security of the protected networks and machines.
2.2.) The firewall issue how to see it can be implemted in DMZ, trust- and Untrusted network.
I hope I have fairly understand it ![]()
Scrum Overview
 Our Scrum table consists of 4 different zones with the needed 4 iterations to complete the project.They are fairly straightforward, but just in case:
Our Scrum table consists of 4 different zones with the needed 4 iterations to complete the project.They are fairly straightforward, but just in case:
First Column: IDEAS/TASKS
For each iteration tasks or ideas will be placed in each field so that we know what we want or are going to do.
# In the regard that each person is obliged to have his own task and to complete it, TASKS/IDEAS will have the name of the person that is responsible for it’s implementation when it is shifted to IN PROGRESS.
Second Column: IN PROGRESS
Starting each iteration there will be assigned tasks from the first column. This basically means that we have started work on the Tasks at hand.
Third Column: DOING TESTS
Signals testing phase of the allotted tasks. In this phase there should be group discussions whether it is done correctly or not.
Fourth Column: DONE
Simple enough. Any tasks after testing shall be moved here if the group considers them to be completed. Moving tasks in the DONE column will only be done by group consent and in group meetings.
Presentation dates
Presentations of progress in project is made in each iterations end.
Dates for presentations are as follow:
1 march
4 march
11 march
18 march
Team tasks in first iteration
Tasks for members through 1 iteration (from 18 feb til 1 march).
Person
Research on DMZ (demilitarized zone) and firewalls in general
Install Monowall firewall, explore, test it
Install Pfsense and FTP server
Research on DMZ (demilitarized zone) and firewalls in general
Person
Install web server
Research on DMZ (demilitarized zone) and firewalls in general
Person
Install virtual environment client, server, pfsense configure, get to know how system works
Research on DMZ (demilitarized zone) and firewalls in general
Person
Research on DMZ (demilitarized zone) and firewalls in general
Install IpCop firewall, explore, test it
Create and configure network
Be able to communicate during week 8, post your progress, problems on blog so members can track your progress.
Task are subject to change and can be specified in progress!